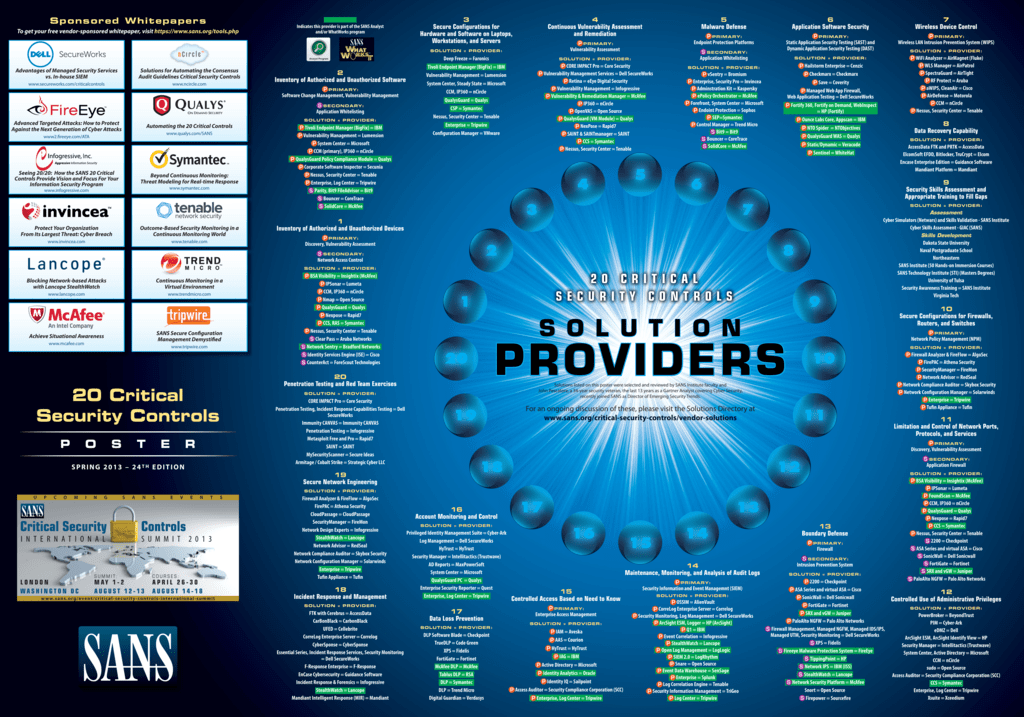
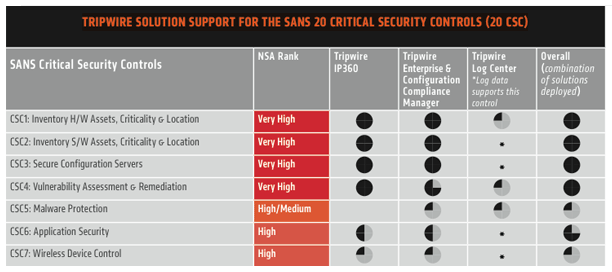
SANS Institute 在Twitter 上:"POSTER | SANS 20 CRITICAL SECURITY CONTROLS - DL & Print crucial info for defending your org. http://t.co/MbpeDjiwRz http://t.co/nqWx9oRl5t" / Twitter
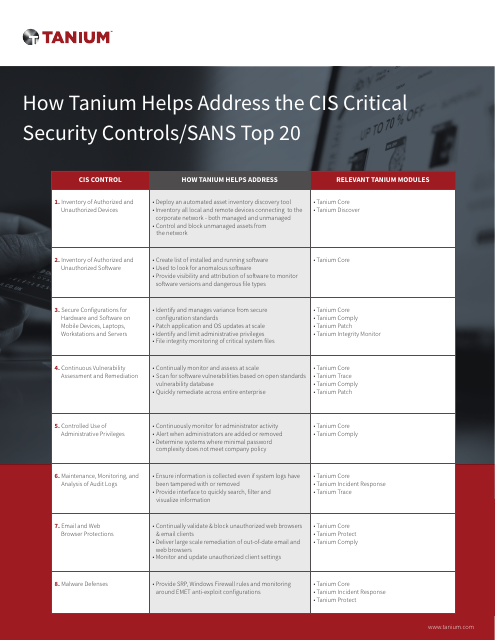
How Tanium helps address the CIS Critical Security Controls/SANS Top 20 | Cyentia Cybersecurity Research Library

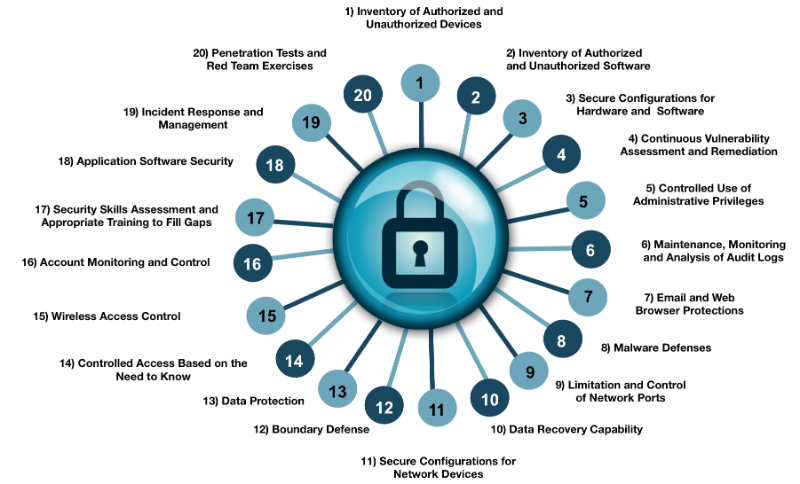
Twitter 上的Michael Fisher:"What are the top 20 controls for a healthy network #Security posture? {Infographic} #CyberSecurity #infosec #education #DevOps #Malware #databreach #Pentesting #IRP https://t.co/M6bSaA0361" / Twitter